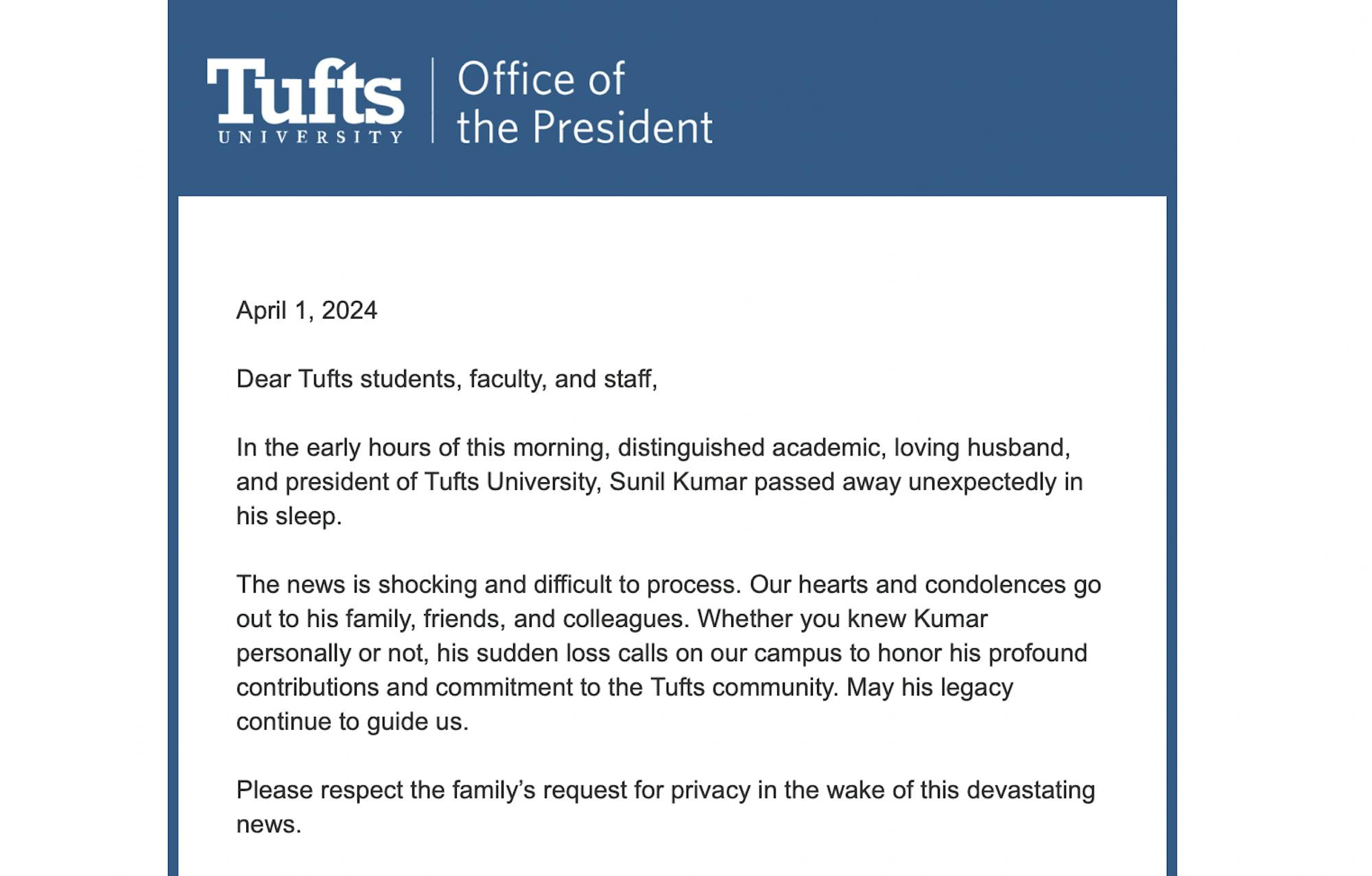
An unauthorized email purportedly announcing the death of University President Sunil Kumar was sent to Tufts community members on the morning of April 1, ending with the words “April Fools” and a call for heightened security measures.
“Tufts Technology Services (TTS) should consider implementing a CAPTCHA service to prevent a simple program from scraping the Tufts directory for emails. Despite being aware of the vulnerability for months, TTS failed to take actionable steps to prevent scraping. As a result, Tufts students and faculty receive spam and phishing emails on a daily basis,” the email, sent by an unknown source, read. “Maybe, the death of the university president will cause TTS to wake up.”
The Office of the President and TTS sent two emails shortly after, assuring the community that the news of Kumar’s death was not true and that the university would investigate the email’s origins. Marty Ray, vice president for strategic initiatives and Kumar’s chief of staff, wrote that the email seemed to be “an ill-advised attempt at an April Fools joke” and clarified that “President Kumar is doing fine and at work on behalf of the Tufts community.” TTS called the email a “sick and awful April Fool’s joke.”
In an email to the Daily, Patrick Collins, Tufts’ executive director of media relations, emphasized that TTS is taking steps toward solving the continued issue of email security breaches.
“The prank was in poor taste and needlessly alarmed people. TTS will explore how this could have happened and address the system vulnerability in question,” he wrote. “We will take action as appropriate.”
Associate Teaching Professor of Computer Science Ming Chow and junior computer science major Michael Daniels, one of Chow’s students, are working to independently investigate the cybersecurity issues presented in the email. Daniels explained why having an open directory without greater protections is potentially dangerous.
“The directory doesn’t seem to care if you are requesting a lot more [information] than a human would need,” Daniels said. “It doesn’t have anything to slow it down or require you to fill out a CAPTCHA or even log in.”
According to Daniels, this method of obtaining large quantities of information and email addresses from the directory may have led to scam emails circulating among the Tufts community. Many of these emails claim to be from faculty members recruiting students for employment positions.
One such scam email was sent to computer science students on March 15, which claimed to have proof of the recipients’ engagement with pornographic materials in an attempt to extort money from them via cryptocurrency. While this email had an explicit motive, the rationale behind the April 1 email appears less clear, Chow said.
“We don’t know because this one was left in extremely bad taste,” Chow said. “I get it’s an April Fools’ joke, but it’s not even a good April Fools’ joke.”
The investigation, however, is still in its early stages.
“In terms of investigation, the furthest that I can go is to the domain that they registered and then seeing if they left any information there,” Daniels said. “They don’t leave any public information. But the registrar, the people who you buy the domain from, do store information about whoever has registered it and gives that, on request, to someone who might have a legal issue — which this is.”
While the pair are unsure who the culprit is, they theorize that the fake email originated from someone with connection to the Tufts community, since the emails have specific information related to Tufts and formatting that mirrors legitimate emails sent out by the administration.
However, the two of them believe that the perpetrator was not a student in Chow’s Introduction to Security class. In the class, they discuss what the necessary action would be upon recognition of a security breach or vulnerability in a system and how to responsibly disclose the issue.
“I have a pretty good recollection of who [approaches me] and with what vulnerabilities,” Chow said. “This does not ring a bell.”